The software company, sodge IT, has high-security demands and thus invests a large amount of time in security testing. Especially open-source components frequently pose a security risk in their supply chain. They simply cannot risk shipping vulnerable software to their customers.
For this reason, their developers had to regularly spend weeks reviewing these open-source components, which significantly slowed down their development process. To solve this issue, the developers were hunting for a way to make their security testing more efficient and effective. In the end, continuous fuzzing helped them to speed up their development process and to make the open-source components in their supply chain more reliable and secure.
Improving Security Tests
sodge IT automated their security testing process, by implementing the CI Fuzz testing platform into their CI/CD. The automation helped them to instantly find and fix three new vulnerabilities in the ZINT Barcode Generator, one of their most important open-source components (CVE-2020-9385, CVE-2021-27799, CVE-2021-39247). Furthermore, the automation also simplified sodge IT's testing processes and enabled their developers to test their software with dynamic inputs.
"We have always been looking for a better solution than our scripts to automate fuzzing in our CI. CI Fuzz is a good solution with a very nice integration in VS Code."
Götz Martinek, Managing Director, sodgeIT
About ZINT
ZINT is a barcode encoding library supporting over 50 symbologies including Code 128, Data Matrix, USPS OneCode, EAN-128, UPC/EAN, ITF, QR Code, Code 16k, PDF417, MicroPDF417, LOGMARS, Maxicode, GS1 DataBar, Aztec, Composite Symbols, and more. (Source: Github)
SodgeIT is highly concerned about the security and reliability of this project since one of their customers may use it in an upcoming product. In order to test the library efficiently and automatically, sodgeIT thought about implementing feedback-based fuzzing as a dynamic testing method for ZINT.
Two main challenges of implementing feedback-based fuzzing involve the high amount of manual effort and the required fuzzing expertise. Often, developers need days or even weeks to get fuzzing tools like AFL or libFuzzer up and running. Despite the immense workload required, sodgeIT wanted to benefit from fuzzing without diverting resources from other high-profile projects. This is when Code Intelligence came in.
Fuzzing ZINT in One Day
In the course of one day, we got this unknown project going. In order to use fuzzing, so-called fuzz targets have to be written. Fuzz targets are small programs that test predefined API functions, similar to unit tests. However, the inputs are not provided by the developer but produced with a fuzz generator based on the feedback from instrumentation.
For this project, we were able to test all the different barcode generation algorithms with a single fuzz target. Derived from existing unit tests, a good entry point (ZBarcode_Encode) was suggested with our software so that we were able to quickly set up fuzzing in the user interface with our "Fuzz this function" feature. Thereby, the manual effort was reduced to a minimum. After defining this fuzz target, the entire application will be fuzzed on every git commit with our testing platform.
Fuzz this Function" automatically creates a fuzz target and resolves all compile-time and link-time dependencies.
Finding a DoS CVE in Minutes
Within the very first minutes of testing, CI Fuzz was able to identify a critical vulnerability. Our testing platform automatically detected a stack buffer overwrite of up to 14 bytes. When entering malicious inputs, provided in the bug report, it would, in the best-base scenario, cause a crash leading to a denial of service (DoS).
If exploited properly, this vulnerability could lead to more severe damage, for example, a remote code execution. The finding was later accepted as a CVE (Common Vulnerabilities and Exposures) with the base score 7,5 (“high severity”). You can find it under the ID CVE-2020-9385.
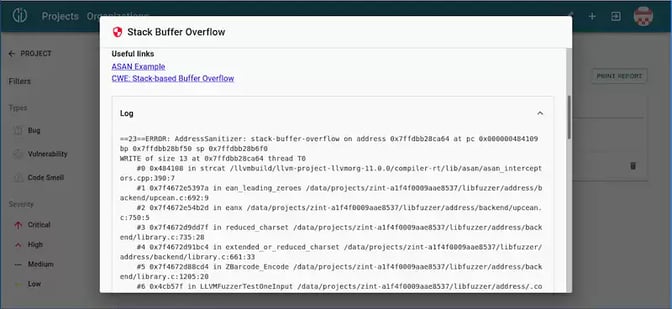 Debugging a stack buffer overflow with CI Fuzz
Debugging a stack buffer overflow with CI Fuzz
After this first run, Nico Gunkel from sodgeIT used CI Fuzz to further investigate the library and reported six additional bugs the following week after. You can find the documentation about all found bugs on Sourceforge.
Open-source software gets often developed by volunteers on a very small budget. It is no shame that this leads to quality and security issues from time to time. Therefore, we believe that testing open-source software really adds value to all participating parties.
By testing open-source projects with Code Intelligence, companies can:
- Assure that the open-source modules, which they are using regularly in their products, are safe and sound.
- Contribute quality improvements to the open-source community.
- Evaluate the benefits of CI Fuzz without sharing their own intellectual property.
As a result of this project, we were able to convince sodgeIT of the added value of our solution and made a valuable contribution to improving Zint.
Fuzz Your Open-Source Projects
In the future, sodgeIT and Code Intelligence want to further expand their partnership. sodgeIT, as a software development company, is convinced that early testing in the development process prevents follow-up costs. Therefore, Code Intelligence can support sodgeIT securing its customers with a solution for early and continuous software testing.
Code Intelligence now offers the opportunity to test open-source components for security and quality issues. Simply sign up with GitHub to access our demo platform and to onboard projects that you want to see fuzzed.

