Many people believe that fuzzing is only useful for C/C++ code because they associate it mainly with finding any kind of bugs that occurs when developers actively manage the memory (memory leaks, buffer overflows, etc.). This is certainly one of the reasons why there are no OSS tools in the field of java fuzzing yet.
Code Intelligence's testing platform, CI Fuzz, includes one of the first Java fuzzers ever and efficiently integrates open-source tools such as the Web App Scanner OWASP ZAP, which enables an even more effective bug detection - even for Java code. In this blog post, we want to explain which vulnerability types can be found with CI Fuzz in Java web applications.
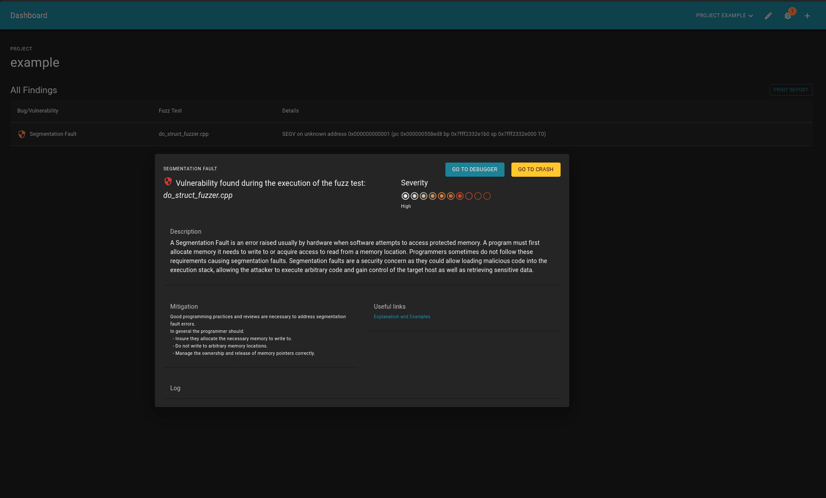
Image: Detailed Bug View of the Testing Platform 'CI Fuzz'
List of Most Typical Vulnerabilities
1. Injections (using the example of SQL injection)
An SQL injection is a very common attack where the user can insert SQL statements into the input data provided to an application. If this input is not properly sanitized, the application executes attacker-controlled statements on the database enabling the attacker to steal sensitive information or change the data.
The instrumentation of CI Fuzz closely checks the application's interaction with the database. By dynamically intercepting all method invocations that interact with the database, CI Fuzz examines the SQL query that is about to be executed. If this query is malformed, an error can be reported to the user. Also, read our blog post Are SQL injections still a thing?
2. Cross-Site Scripting (XSS)
XSS vulnerabilities can lead to external malicious scripts being executed from your trusted web application. Using battle-tested XSS detection algorithms in tandem with the smart input generation employed by CI Fuzz, which maximizes code coverage, the platform finds more sophisticated XSS vulnerabilities compared to traditional methods. For this purpose, CI Fuzz combines the power of smart fuzzing with proven XSS detection mechanisms through the integration of OSS tools as the web application security scanner OWASP ZAP.
3. Infinite Loops / Timeouts
Infinite loops and unlimited recursion can easily happen in unsuspecting situations, which might have been missed by the unit test cases. Using the coverage-based feedback, CI Fuzz will specifically craft inputs that trigger such cases and report them as memory leaks.
4. Information Leaks
Your application should never disclose more information about itself than it needs to. Providing unnecessary information (e.g. in an error response) can give a malicious attacker a leg up and make it possible to craft more sophisticated attacks. Therefore, CI Fuzz checks each server response for sensitive information such as stack traces, URLs, file paths… and reports them as possible vulnerabilities. The unique advantage of feedback-based fuzzing lies in the power of detecting corner cases that other tools can easily miss.
5. Memory Management Errors (OutOfMemoryError, Garbage Collector, etc)
Basically the same as for Information Leaks: Using feedback-based fuzzing, corner cases can be found which can trigger e.g. “OutOfMemoryError: GC overhead limit exceeded” and indicate that the garbage collector is performing inefficiently. Often these types of errors are not uncovered by manual tests in the test environment but only on a production system with a full load. Additionally, fuzzing acts as a stress test which will give you more confidence that the application will survive production load.
6. Insecure Deserialization
Insecure Deserialization allows an attacker to send specifically designed messages that are processed on the server-side and can lead to remote code execution, DOS vulnerabilities, etc. By understanding the format of the serialized message CI Fuzz can generate new inputs according to this format and therefore more efficiently uncover vulnerable inputs (also called grammar fuzzing).
7. XML External Entities (XXE)
For XML External Entities basically the same as for Cross-Site Scripting (XSS) applies: The testing platform CI Fuzz nudges OWASP ZAP in the right direction and, therefore, combines powerful bug detection algorithms with feedback-based fuzzing.
8. Path Traversal
A path traversal attack (directory traversal) aims to access files that are stored outside the web root folder. These allow an attacker in the worst case to read and possibly write to the entire file system of the server. By checking all file operations for user input we can reliably detect path traversal vulnerabilities.
9. DOS Vulnerability
Denial of Service (DoS) vulnerabilities are often a consequence of Infinite Loops / Timeouts or Memory Management Errors. CI Fuzz detects and reports any requests/inputs that take an unusually large time to process by the server application. Such requests could be used by an attacker to perform a denial of service (DOS) attacks.
10. Unhandled Exceptions
Any type of unhandled exception (e.g. Runtime Exceptions: NullPointerExceptions, ArrayIndexOutOfBounds Exceptions, BufferOverflow Exceptions, NumberFormatExceptions, …) can be detected with fuzzing very well. Using coverage-based fuzzing with sophisticated input mutation it is possible to uncover unexpected program states leading to exceptions that were explicitly dealt with by the programmer and could lead to security vulnerabilities. In a typical web application, an unhandled exception results in a 500 response which is not helpful to the user. Some of these exceptions could be classified as bugs, but they can also show logical errors that might be exploitable by an attacker.
Want to learn more about the opportunities of fuzzing? Book a call with one of our security experts! We will walk you through the process and answer your questions.

