How sodge IT accelerated their development process by implementing automated security tests in their CI/CD, and fixed critical vulnerabilities in their supply chain.
Industry
Software Development
Department
Development
Size
> 10 Employees
Location
Balingen, Germany
The Results
A Secure Software Supply Chain
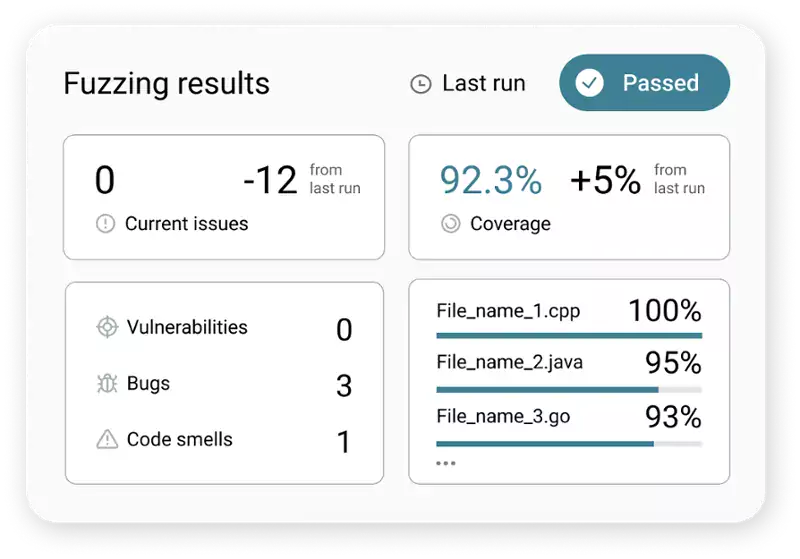
sodge IT was looking for a way to make their security testing more efficient and effective. Continuous fuzz testing helped them to speed up their development process and to make the open-source components in their supply chain more reliable and secure.
Fixed 3 CVEs in Open-Source Critical Component
Less False Positives
The Challenge
Simplified Use of Advanced Fuzzing Practices
Thus, sodge IT was highly concerned about the security and reliability of an open-source project that one of their customers wanted to use in an upcoming product. In order to test this library, sodgeIT thought about implementing feedback-based fuzzing as a dynamic testing method, but they faced two major challenges.
Manual Effort
High Complexity
The Solution
The CI Fuzz Testing Platform
Increased Automation
Broad Application Testing










The Success
Fixed Critical Vulnerabilities In Open-Source Component
Within the very first minutes of testing, CI Fuzz managed to identify a critical vulnerability in one of its critical open-source components (ZINT Barcode Generator). This testing platform automatically detected a stack buffer overwrite of up to 14 bytes.
When entering malicious inputs, provided in the bug report, it would in the best-case scenario cause a crash leading to a denial of service (DoS). If exploited properly this vulnerability can lead to more severe damage, for example, a remote code execution. At the end of the story, the finding was accepted as CVE-2020-9385 with a base score 7,5 (“high severity”).