Since the outbreak of the COVID-19 pandemic, tracing apps have been discussed in order to better track the spread of the virus. Critics of these apps have mainly expressed concerns regarding the security and privacy implications for the end-users.
The DP3T backend, which is for example used in the tracing app SwissCovid, is open-source, non-profit, and developed for a good cause (better understanding and controlling of the COVID-19 pandemic). That’s why we at Code Intelligence decided to take a look at the backend on our own and get it tested.
DP3T: The Tracing Backend of SwissCovid
On the 25th of May, Switzerland's Federal Office of Public Health launched the pilot phase of their COVID-19 tracing app SwissCovid and started offering it for iOS and Android. SwissCovid for Android can be downloaded and installed directly from the Google Play Store. The backend for SwissCovid is dp3t-sdk-backend.
The Decentralised Privacy-Preserving Proximity Tracing (DP3T) project is an open protocol for COVID-19 proximity tracing using Bluetooth Low Energy functionality on mobile devices, which ensures that personal data and computation stay entirely on an individual's phone. The backend is based on Java 11 and Spring Boot 2.2.6.
Screenshots of SwissCovid, an open-source app utilizing the dp3t-sdk-backend
Using Fuzzing to Detect Security Risks
Since the release of CI Fuzz for the Java Spring Boot framework in December 2019, we at Code Intelligence are working hard to increase the security of customers' Spring Boot applications.
Using CI Fuzz, Code Intelligence’s testing platform which is based on feedback-based fuzzing, our engineer Simon Resch found several bugs and vulnerabilities and reported them to the maintainers of the open-source project. You can find the full pull request here.
Among the list of reported issues were mostly unhandled exceptions or incorrect error handlings, which could make the backend prone to denial of service (DoS) attacks. In the worst case, this could have led to a shutdown of the app. Additionally, there was one case of error handling that would return unsanitized HTML upon parsing errors.
Bugs of this type could lead to successful XSS attacks if the API is included in an unsafe way. To better understand these kinds of errors, think of an API, which only accepts numbers as parameters. When you send a request containing something like <script>alert(‘evil’)<script> instead of a number, the error message should not display the wrong input without sanitizing it. If it does, this leads to reflected cross-site scripting. Here is a write-up about reflected XSS at OWASP.
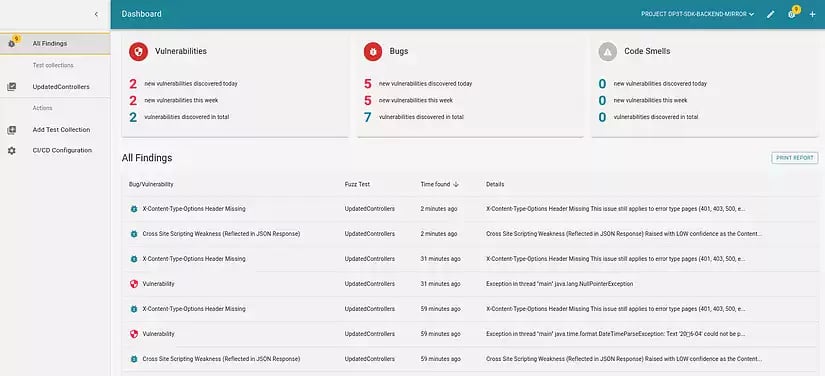 The findings in DP3T as shown in CI Fuzz
The findings in DP3T as shown in CI Fuzz
Summary
The backend DP3T was securely implemented to a large extent. Nevertheless we were able to find some issues. Today our suggested improvements to address these issues were accepted and merged by the maintainers. Thereby we could contribute to making the backend of SwissCovid more secure. Code Intelligence is looking forward to continuing testing open-source projects and thereby supporting the open-source community.
About CI Fuzz
Code Intelligence’s testing platform, CI Fuzz, enables developers and software testers to easily create and continuously execute security and reliability tests by automating application security testing. CI Fuzz decreases the amount of security knowledge needed and helps leading global companies such as Bosch, Deutsche Börse, and Deutsche Telekom to make their software secure and reliable.
The technology component at the core of CI Fuzz is feedback-based fuzzing which is a dynamic testing technique that uses smartly generated inputs to detect bugs and vulnerabilities. Code Intelligence develops a cutting edge and usable form of fuzzing. Therefore, bugs and vulnerabilities are detected early and automatically in the development process, reducing the time-to-market and costs for development teams.
Book a demo with one of our security experts, and watch our CI Fuzz in action.

